How to Spot and Avoid Fake Invoice Templates
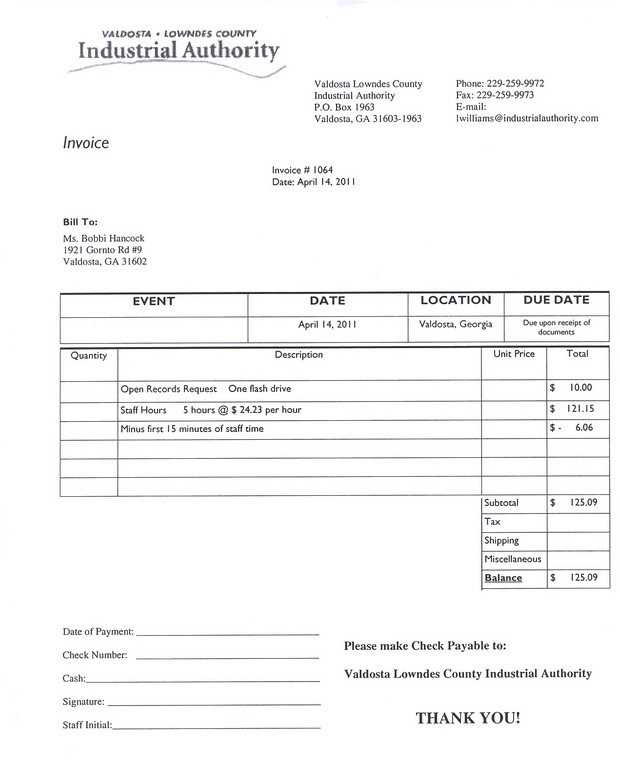
Businesses and individuals face increasing challenges when it comes to distinguishing between legitimate and fraudulent financial documents. These deceptive practices can lead to significant losses, damaging both finances and reputation. Understanding how these misleading documents are crafted and the tactics used by scammers is crucial to preventing such occurrences.
Recognizing fraudulent documents often requires a keen eye for detail. They may appear similar to legitimate records, but subtle differences can expose their deceptive nature. Knowing what to look for, from the layout to the content, can help identify these malicious attempts before any damage is done.
While technology continues to advance, so do the methods used by criminals to create convincing counterfeit documents. This article will delve into the most common indicators of fraudulent financial records and provide you with the tools to protect yourself and your business from falling victim to these scams.
Understanding Fraudulent Billing Documents
Fraudulent financial records are carefully crafted to appear legitimate, often deceiving businesses and individuals into making payments. These documents are designed with a level of detail that mimics authentic paperwork, making it difficult to distinguish them from genuine transactions. The key to identifying these deceptive records lies in understanding the common tactics scammers use to create them.
Fraudsters typically base their counterfeit documents on real-world formats, borrowing elements such as logos, fonts, and even the structure of legitimate bills. This creates a false sense of credibility and increases the likelihood of the recipient trusting the document without question. However, there are usually subtle discrepancies in formatting, contact details, or even the language used that can serve as a clue.
Recognizing the signs of deception requires a critical eye. The more familiar you are with how legitimate financial documents are structured in your industry, the easier it becomes to spot unusual patterns or inconsistencies. This section will help you identify these red flags and understand the methods behind these fraudulent practices.
Common Signs of a Fraudulent Billing Document
Identifying deceptive financial records can be challenging, but certain characteristics can give them away. Fraudulent documents often contain subtle errors or unusual features that make them stand out from legitimate ones. Being aware of these common signs can help you avoid falling victim to scams.
- Unusual Sender Information: The contact details of the company or individual may be incorrect, missing, or hard to verify. Often, scammers use generic email addresses or phone numbers that do not match the official company details.
- Missing or Incorrect Details: A legitimate financial document typically includes specific details such as a unique reference number, full business addresses, tax identification numbers, and a clear breakdown of charges. Fraudulent documents may lack one or more of these key pieces of information.
- Inconsistent Formatting: Look for irregularities in the layout, fonts, or alignment. Scammers may not be able to replicate the polished formatting of a legitimate business document, which could include spacing issues, incorrect logos, or awkward text placement.
- Errors in Language or Grammar: Poor grammar, spelling mistakes, or awkward phrasing are red flags. Authentic businesses take care to ensure their documents are professionally written, so any deviation from this standard is suspicious.
- Pressure to Pay Quickly: Fraudulent documents often create a sense of urgency, pushing you to make a payment immediately. A legitimate business transaction usually allows a reasonable timeframe for payment without aggressive follow-ups.
By recognizing these common warning signs, you can protect yourself and your organization from falling prey to deceptive financial schemes.
Why Fraudulent Billing Documents Are Dangerous
Deceptive financial records can lead to serious consequences for both businesses and individuals. These documents are often used as a tool to manipulate people into making payments or sharing sensitive information, ultimately causing financial harm and damage to reputations. Understanding the dangers of these fraudulent schemes is essential for protecting yourself and your business.
Financial Losses
One of the most obvious risks of falling victim to fraudulent financial records is the potential for significant financial loss. Scammers design these documents to appear authentic, tricking recipients into making payments that they otherwise would not have. These payments can be hard to recover, especially if the fraudster operates from an anonymous or foreign location.
Reputation Damage
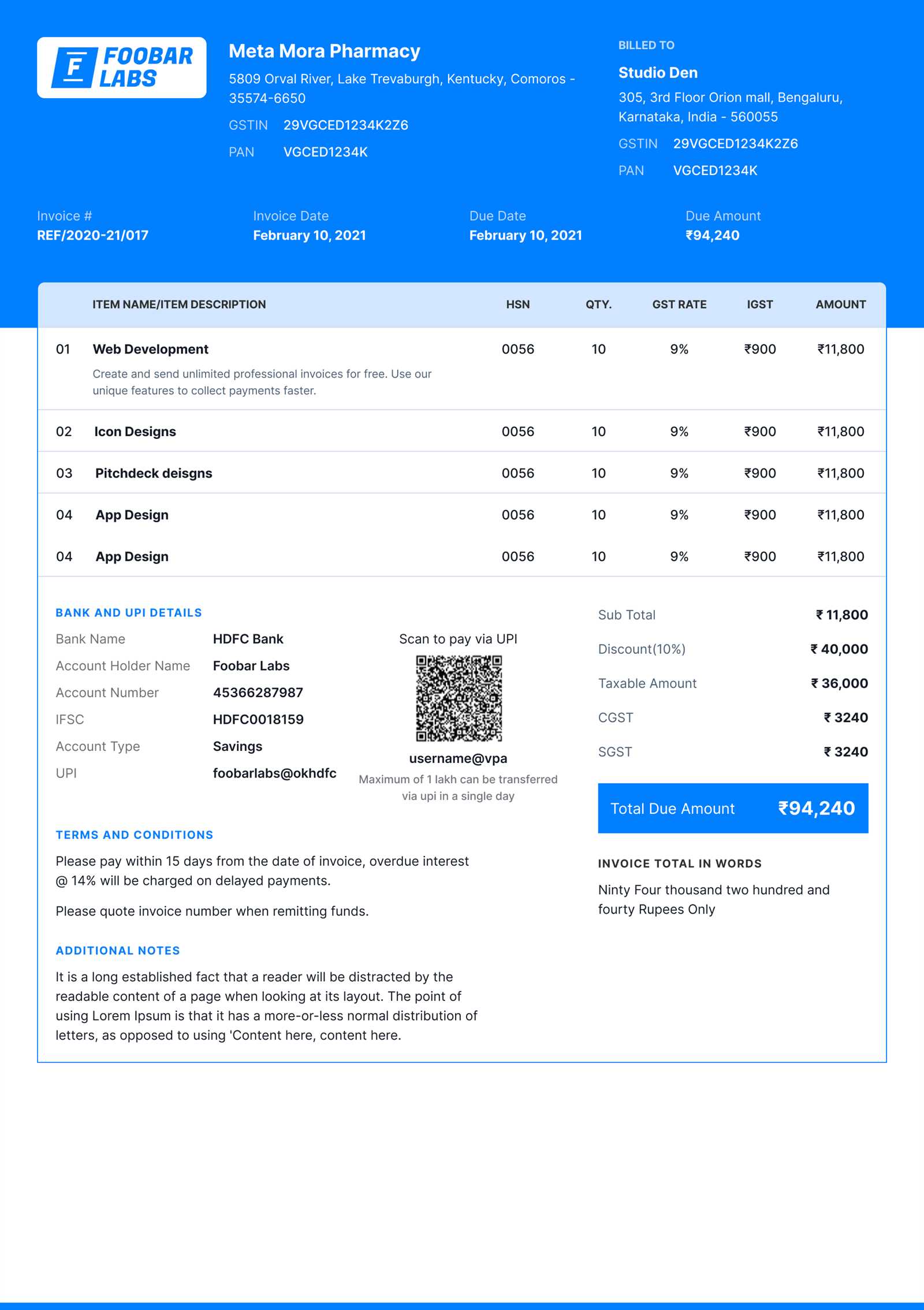
Being associated with fraudulent transactions, even unknowingly, can severely damage a company’s reputation. Once word spreads that a business has been deceived by misleading billing documents, clients, partners, and even the public may lose trust. This could lead to a loss of customers, business relationships, and long-term credibility.
Legal Implications can also arise when organizations fail to recognize fraudulent documents. In some cases, businesses may find themselves inadvertently violating tax or financial regulations, especially if they process payments without verifying the legitimacy of the records. This can result in fines, legal fees, and more serious legal actions.
In summary, the risks of falling victim to fraudulent financial documents go beyond just monetary loss. They can affect a business’s reputation, lead to legal troubles, and create lasting consequences. Recognizing and addressing these deceptive practices promptly is crucial for minimizing harm.
How Fraudsters Create Deceptive Billing Documents
Fraudsters employ a variety of methods to craft convincing financial documents that appear legitimate. These documents are often designed to mimic real business transactions closely, using familiar formats and language to deceive the recipient. Understanding the tactics used by scammers can help businesses stay alert and recognize these deceptive attempts before any harm is done.
Replicating Authentic Designs
One common tactic is to replicate the design and layout of genuine billing documents. Fraudsters often use readily available software to create documents that closely resemble those of well-known companies. This includes using official logos, fonts, and templates that mimic the real thing. The goal is to trick the recipient into thinking they are dealing with a legitimate request, thereby increasing the chances of payment.
Exploiting Trusting Relationships
In many cases, scammers exploit existing relationships with businesses to increase their credibility. For example, they may use a known supplier’s name or reference a previous transaction to make their documents seem more authentic. By creating a sense of familiarity, fraudsters increase the likelihood that their request will be processed without question.
Advanced Social Engineering techniques are also often employed. Scammers may research the target company or individual to learn specific details about the business, such as billing practices or payment cycles. This information is then used to make the fraudulent document appear more realistic, making it harder to detect.
Overall, fraudsters are constantly refining their methods to produce increasingly convincing documents. By understanding how they operate, businesses can take steps to verify financial documents and avoid falling victim to these deceptive practices.
What to Do if You Receive One
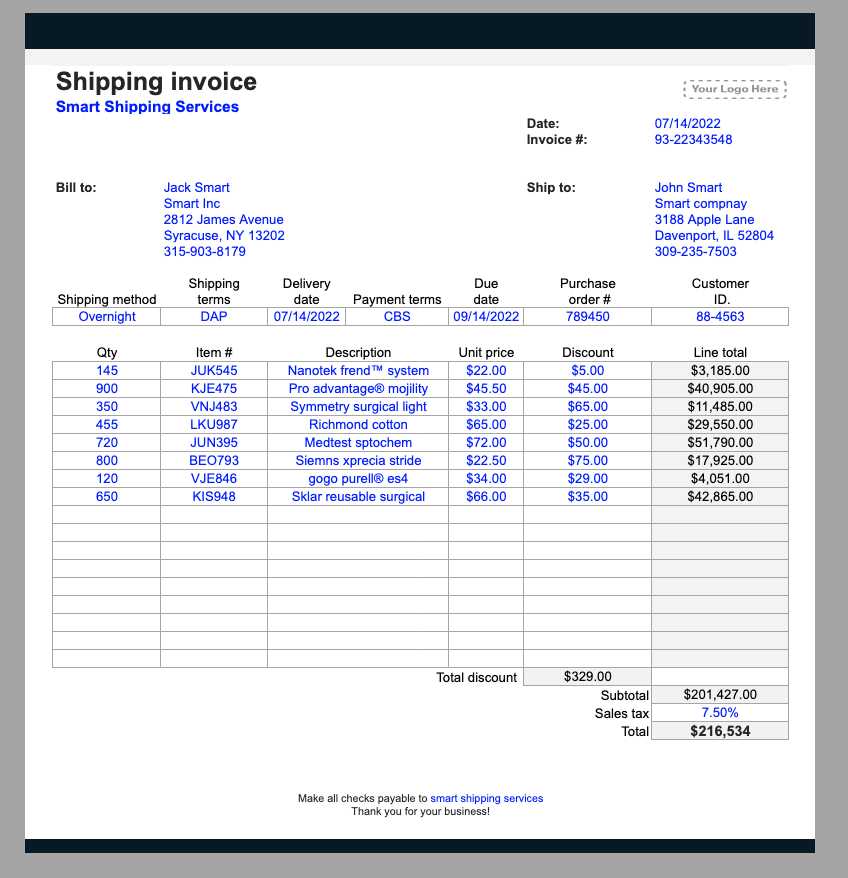
Receiving an unexpected document resembling a payment request can be concerning, especially if you’re unsure of its origin or authenticity. It’s essential to handle such documents carefully to avoid potential risks. Here are steps to verify and respond appropriately.
- Review the Details: Check the sender’s information, contact details, and the services or items mentioned. Ensure they align with previous interactions or known agreements.
- Cross-Check with Past Records: Search through past documents to confirm if there is a legitimate basis for the request. This may include contracts, agreements, or correspondence.
- Contact the Source Directly: If any information appears questionable, reach out to the company or individual listed using official contact details from their website or known sources. Avoid using contacts provided in the document itself.
- Report Suspicious Activity: If the document raises red flags and you cannot confirm its validity, consider notifying relevant authorities or reporting it to a consumer protection agency.
By following these steps, you can better
Preventing Fake Invoice Scams in Your Business
Protecting your business from unauthorized financial requests requires proactive measures and awareness. Implementing robust verification practices can significantly reduce the risk of falling victim to misleading billing schemes. Below are strategies to help safeguard your organization.
- Establish Verification Procedures: Set up a process where all payment requests go through multiple levels of approval. This ensures that only verified documents are processed.
- Train Your Team: Educate employees on recognizing suspicious documents and the importance of confirming legitimacy before making any transactions.
- Maintain Supplier Records: Keep an updated list of approved vendors and clients, with contact details easily accessible for verification purposes.
- Implement Digital Security Measures: Use software that automatically checks document authenticity and flags anomalies, providing an additional layer of security.
- Encourage Open Communication: Ensure team members feel comfortable questioning any unusual requests without fear, promoting a vigilant workplace culture.
How to Verify an Invoice’s Authenticity
Ensuring that a received billing document is genuine can protect your business from unauthorized payments and financial risks. By following a systematic approach, you can confirm the legitimacy of the request. Here are essential steps to verify authenticity.
- Check Sender Details: Review the contact information, company name, and address listed. Cross-reference this information with official sources, such as the company’s website or previous communications.
- Confirm Itemized Charges: Carefully examine the listed items or services, verifying they align with known purchases or agreements. Any unfamiliar charges should be clarified before payment.
- Verify Account and Payment Instructions: Ensure that bank account details and payment methods match those on file. Changes to payment information should raise immediate caution and be validated independently.
- Cross-Check with Relevant Departments: In larger organizations, coordinate with accounting or procurement to confirm if similar documents have been processed or if there is an established relationship with the sender.
- Contact the Issuer Directly: If any doubt remains, reach out to the source using trusted contact methods, not those provide
Legal Consequences of Fake Invoices
Issuing or processing unauthorized payment requests can lead to significant legal repercussions. Both businesses and individuals involved in such activities may face serious consequences under the law. Below is a breakdown of potential legal outcomes associated with fraudulent billing practices.
Consequence Description Fines and Penalties Organizations found responsible may be subjected to substantial fines, which vary based on the severity and jurisdiction. These financial penalties are intended to deter fraudulent practices. Criminal Charges In cases involving deliberate deception or large sums, individuals may face criminal charges. Convictions can result in prison sentences and a permanent record, affecting future employment and business opportunities. Civil Liability Spotting Red Flags in Invoice Formats
Recognizing irregularities in billing documents can help prevent unauthorized transactions. Certain details within the document layout and content often signal potential issues. Here are key areas to inspect closely when evaluating payment requests.
Unusual or Missing Information
- Incomplete Contact Details: Verify that the sender includes complete and accurate business information, including address and official contact methods. Missing or vague details can be a warning sign.
- Lack of Company Branding: Authentic documents generally include company logos, consistent fonts, and clear branding. An absence of these elements or a mismatch in styling can indicate problems.
- Inconsistent Reference Numbers: Double-check reference or document numbers against past records. Unexpected formats or sequences may point to a suspicious request.
Inaccuracies in Itemized Charges
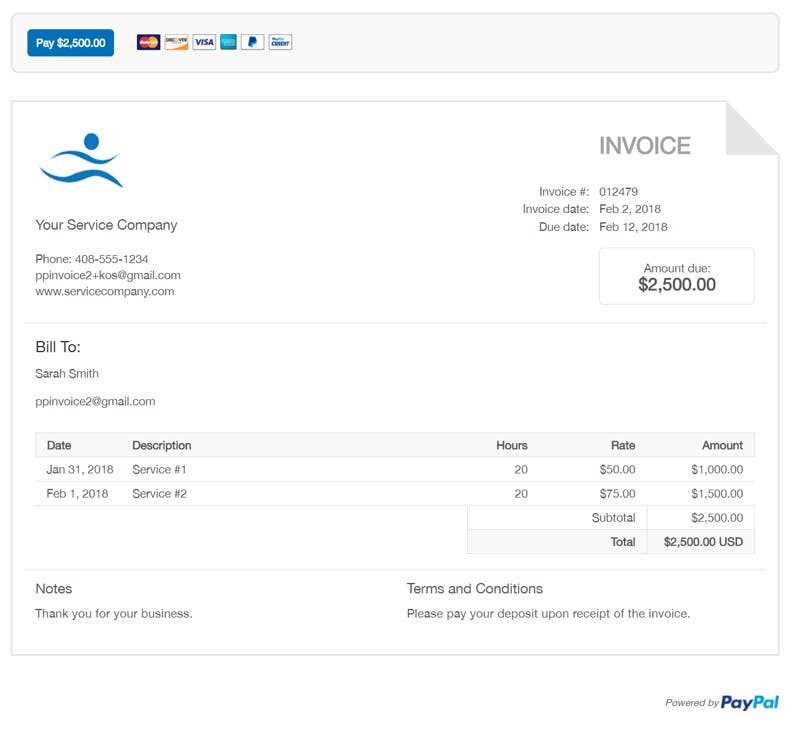
- Unfamiliar Descriptions: Examine the descriptions of items or services. Vague or overly generic terms m
How to Report Fake Invoices
Encountering a suspicious billing request requires a prompt and structured response to prevent further issues and protect others. Reporting such incidents can help authorities take appropriate action and alert other potential victims. Below are recommended steps for reporting questionable payment requests.
Step Description Document the Details How to Report Fake Invoices
Encountering a suspicious billing request requires a prompt and structured response to prevent further issues and protect others. Reporting such incidents can help authorities take appropriate action and alert other potential victims. Below are recommended steps for reporting questionable payment requests.
Step Description Document the Details Save copies of the document and any related correspondence. This includes emails, phone records, or messages that could provide context for the report. Contact Your Financial Institution Notify your bank or financial provider about the suspicious request. They may help in monitoring transactions and preventing unauthorized transfers. Report to Relevant Authorities Submit a report to consumer protection agencies or fraud monitoring organizations. Many countries have dedicated fraud-reporting centers that handle such cases. Inform Your Legal Department If applicable, engage your legal team or consult a lawyer to ensure appropriate actions are taken, especially if personal or company information was disclosed. Notify Business Partners If you suspect a broader scheme, inform relevant business contacts or clients to help them avoid similar risks and strengthen their own verification processes. By following these steps, you can assist in preventing fraudulent activities and contribute to broader awareness, reducing risks for others.
Fake Invoice Templates and Tax Risks
Improper billing documents can lead to significant tax-related complications for businesses. When false payment requests are mistakenly recorded in financial records, they can expose companies to audits, fines, and reputational damage. Below are some of the tax risks associated with processing fraudulent financial requests.
Risk Description Incorrect Tax Deductions Recording an unauthorized payment request as a legitimate expense may lead to incorrect tax deductions, which can result in financial discrepancies during an audit. Liability for Tax Evasion If fraudulent transactions are discovered, a business may be held liable for tax evasion, leading to heavy penalties and possible legal action Steps to Take After Paying a Fake Invoice
If your business has unintentionally processed a fraudulent payment, taking swift action is crucial to minimize potential financial losses and prevent similar incidents. By following specific steps, you can work to recover funds and strengthen your defenses against future attempts.
Contact Your Financial Institution
Immediately reach out to your bank or payment provider to report the unauthorized transaction. Many institutions have procedures for handling fraud cases, and they may be able to halt or reverse the payment if caught in time. Ensure you have all necessary details, including transaction dates, amounts, and any relevant communications, to support your claim.
Gather Documentation and Evidence
Compile all records associated with the transaction, such as emails, contracts, and billing statements, as these will be essential for any legal actions or internal audits. Accurate documentation helps identify how the incident occurred and can serve as evidence if you need to report the fraud to authorities.
- Impersonation: Fraudsters may use email addresses that closely resemble those of trusted contacts or known vendors, creating a false sense of authenticity.
- Urgent Requests: Messages often stress urgency to bypass normal verification procedures,
How Technology Helps Detect Fake Invoices
Modern technology plays a crucial role in identifying and preventing fraudulent billing practices. By leveraging advanced tools and automated systems, businesses can analyze transactions more accurately, reducing the likelihood of unauthorized payments slipping through. Understanding how these technologies work can empower organizations to safeguard their financial operations.
Automation and Data Analysis
Automated systems are highly effective at scanning vast amounts of financial data for inconsistencies. They can detect unusual patterns, flagging discrepancies that might otherwise go unnoticed. Common methods include:
- Pattern Recognition: Software can identify irregularities by comparing current entries with previous records, helping spot unusual amounts, dates, or vendor details.
- Machine Learning: Machine learning algorithms adapt over time, learning from past cases to recognize new signs of f
Educating Employees About Fraudulent Billing Practices
One of the most effective ways to prevent financial losses in a company is by ensuring that employees are well-informed about deceptive billing schemes. By equipping staff with the knowledge to recognize suspicious financial requests, organizations can minimize the risk of unauthorized payments. Continuous education on how to handle such situations can be key to maintaining secure business operations.
Training Employees to Identify Red Flags
Employees need to be trained to spot signs of fraudulent billing. Regular training sessions should focus on the following key warning signs:
Red Flag Description Unusual Sender Information If an email or document originates from an unfamiliar or altered email address, it may be a sign of fraud. Urgent Payment Requests Fraudulent messages often create a sense of urgency, asking for immediate payment or action. Inconsistent or Missing Details Invoices that lack necessary information, such as specific product details or contact information, may be suspicious. Incorrect Vendor Information Compare vendor details with your existing records. Any discrepancies in addresses or phone numbers should raise concerns. Creating a Response Plan
In addition to training, it’s essential for businesses to develop a clear response plan. Employees should know the exact steps to take when they encounter a potentially fraudulent request, such as:
- Verify the Request: Always double-check with the vendor or supplier before processing any payment.
- Consult with Management: Report any suspicious activity to supervisors or managers before proceeding with any actions.
- Use Secure Communication Channels: When in doubt, use known and secure communication methods to confirm any details related to financial transactions.
By continuously educating employees and providing clear guidelines, businesses can significantly reduce the risks associated with deceptive financial requests.
Understanding the Role of Email in Fraud
Email is a primary tool used by cybercriminals to carry out deceptive activities against businesses. Recognizing the tactics employed in fraudulent emails can help your organization stay vigilant and avoid potential financial loss. Knowing what to look for can make it easier to identify suspicious messages and protect your company’s resources.
Common Tactics in Fraudulent Emails
Cybercriminals often use carefully crafted messages that appear legitimate to trick recipients. They may imitate known contacts, use urgent language, or provide false instructions to encourage immediate action. Some typical methods include: